Global fitness tracker data exposes IoT policy gap

Thanks to data from fitness trackers, jogging routes of service members are providing a virtual atlas of sensitive military installations and forward operational bases around the world.
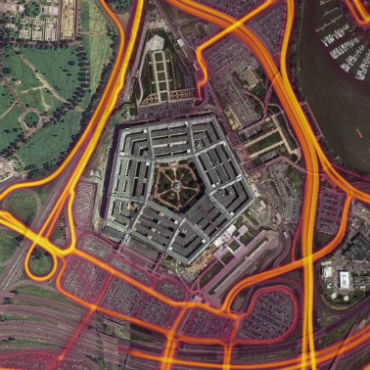
A section of the Strava heatmap shows jogging activity around the Pentagon.
The use of Fitbits by service members is leaving a digital trail of breadcrumbs around some of the world's most sensitive military installations. Analysts and journalists have been able to identify secret or sensitive military posts around the world using fitness tracker data released by Strava in a global heat map.
Fitness trackers are generally permitted under U.S. military rules, with a few conditions. A 2015 Navy policy document explains the basic terms of authorization. The use of receive-only global positioning system data, Bluetooth connectivity, and near-field communication capabilities are ok. Connecting to cellular networks, audio or video recording features and connections to government information systems is not permitted.
"Recent data releases emphasize the need for situational awareness when members of the military share personal information," Department of Defense spokesperson Maj. Audricia M. Harris said in an emailed statement. "DoD takes matters like these very seriously and is reviewing the situation to determine if any additional training or guidance is required, and if any additional policy must be developed to ensure the continued safety of DoD personnel at home and abroad."
Strava's map, first released in November 2017, is based on anonymized aggregate data which is captured during workouts and uploaded to user accounts. Individual users can use their data to monitor their own workouts and share with friends and social media contacts.
Users can go private if they choose. In a statement, Strava said that the heat map "excludes activities that have been marked as private and user-defined privacy zones." The company said in a follow-up statement that it is "committed to working with military and government officials to address sensitive areas that might appear."
The use of anonymized data to identify U.S. military and intelligence activity points to a possible DOD policy gap with regard to the use of personal devices. Most existing policy is aimed at protecting government networks and safeguarding personally identifiable information.
"Annual training for all DoD personnel recommends limiting public profiles on the internet, including personal social media accounts," Harris noted in her statement. "Furthermore, operational security requirements provide further guidance for military personnel supporting operations around the world."
Dave Wennergren, a former DOD deputy CIO, said that despite any formal policy, "I think that implementations and current practices are probably over the map, particularly with the rapid expansion of IoT [and] internet-enabled devices."
Paul Brubaker, another former DOD deputy CIO who studies the regulatory environment around the internet of things as president and CEO of the Alliance for Transportation Innovation, said that the structure of the Department of Defense makes it difficult to pivot quickly to new challenges like that posed by the Strava map.
"Nobody owns it – that's the issue," Brubaker told FCW. "The lack of coordination is staggering and it's got to get better. The pace of technology is advancing so quickly that regulatory guidance and policy can't keep up."
At the same time, leaving it to base commanders to enforce operational security requirements may not be the best answer. "Commanders have a lot of other things on their mind," Brubaker said. "They can't be expected to know the latest and greatest features on apps and devices that their troops may or may not be using."
The Strava issue also has the attention of the White House.
"We'll absolutely be weighing in," Rob Joyce, the cybersecurity lead at the National Security Council, told reporters on the sidelines of a Jan. 29 event. "It's really clear that that heat map is a security risk and the issue with that heat map is the amount of people that could touch that data." But, he added, "that data exists with or without that service being put up on the Internet, and it just shows the connectivity, the data logging and big data opportunities and threats that are around us every day in the world."
In a follow-up tweet, Joyce said that, "While policy evolution is needed, it is important to make good security policy balanced by not overreacting too."
Brubaker said he doubts operational security is much jeopardized by the Strava heat maps, despite the headlines. The fitness data isn't transmitted in real time, he noted, and he expects that local populations in the vicinity of sensitive U.S. bases are already aware of nearby presence. He cautioned against regulatory overreaction.
"A formal policy response is a little bit of overkill," he said. "The bigger question is: What's the best way to approach this game of whack-a-mole that we're going to be playing for several years, if not decades, as we become increasingly connected?"
Personal security may be a different matter. Experts diving deeper into the data are finding ways to link public social media information to jogging and exercise routes near military bases and intelligence agency facilities. The extraction of personal data from anonymized heat maps points to a larger risk inherent in data collection – the ability to hone in on individual service members and intelligence operatives.
"The Strava stuff is obviously just the tip of the iceberg," security analyst Tobias Schneider said on Twitter. "Lots of companies sit on far larger caches but are smart enough to keep the lid on. Now are they also well prepared to protect that data from curious state actors?"
FCW Staff Writer Derek B. Johnson contributed reporting to this article.



