Why cybersecurity remains a risky endeavor
Cybersecurity is a 'tough nut to crack,' and escalating attacks only make it harder.

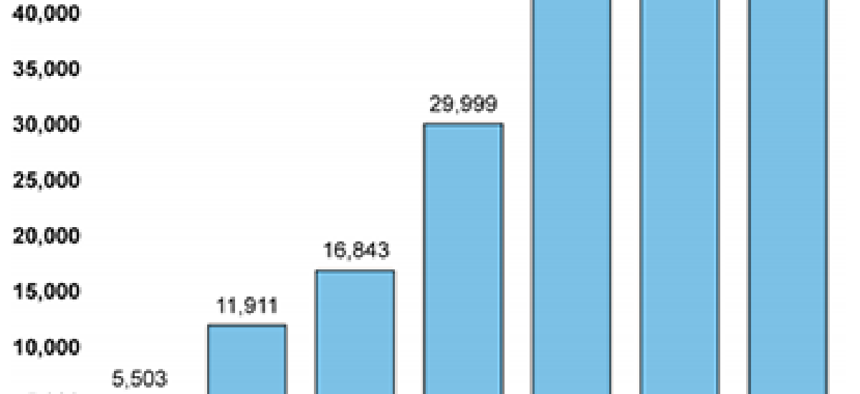
The number of detected cyber incidents has grown year by year. (GAO graphic)
Protecting the federal government’s information systems and cyber critical infrastructures remains on the Government Accountability Office’s latest High Risk List, one of 30 such high-risk government programs and topics outlined in the report released on Feb. 14.
The report details how the vast majority of federal agencies continue to face challenges in effectively implementing cyber-security in the wake of continued increases in sophisticated cyber-attacks that put information systems at risk. While GAO officials report that some progress has been made in curtailing risks posed by these threats, rapidly evolving technologies and agency interconnectedness with the public creates challenges moving forward.
"There have certainly been improvements," said Greg Wilshusen, director of Information Security Issues at GAO. "But this has been on the (High Risk List) for a while. It’s a tough nut to crack."
GAO has listed the federal government’s information systems as "high-risk" since 1997, and in 2003 expanded the risk to include cyber critical infrastructure protection.
Wilshusen cited President Barack Obama’s recent executive order on cybersecurity as progressive for charging heads of agencies to meet specific time-sensitive deliverables, and said recent cross-agency efforts led to the creation of three major priorities to enhance various cybersecurity capabilities.
Yet cyber incidents affecting computer systems and networks have risen dramatically since 2006, when 5,500 such attacks were reported to the U.S. Computer Emergency Readiness Team (CERT).
In 2012, 48,500 such attacks were reported to CERT, an increase of almost 800 percent. Similarly, reports of cyber incidents affecting national security, intellectual property and individuals have been widespread, the report states, with reported incidents involving data loss or data theft, economic loss, computer instructions and privacy breaches.
In addition, 19 of 24 major federal agencies reported material weaknesses or significant deficiencies in internal controls in financial reporting, and inspectors general at 22 of those 24 agencies "cited information security as a major management challenge for their agency," the report states.
Information security weaknesses in most agencies were found in most of five areas, the report states: "Limiting, preventing, and detecting inappropriate access to computer resources; managing the configuration of software and hardware; segregating duties to ensure that a single individual does not control all key aspects of a computer-related operation; planning for continuity of operations in the event of a disaster or disruption; and implementing agency-wide information security management programs that are critical to identifying control deficiencies, resolving problems, and managing risks on an ongoing basis."
In remedying these issues, the report states: "The administration needs to prepare an overarching cybersecurity strategy that includes all desirable characteristics of a national strategy, including milestones and performance measures; cost, sources, and justification for needed resources; specific roles and responsibilities of federal organizations; guidance, where appropriate, regarding how this strategy relates to priorities, goals, and objectives stated in other national strategy documents; and demonstrate progress in implementing the strategies and achieving measureable and appropriate outcomes."
It also calls for Congressional legislation to better define "roles and responsibilities" for overseeing federal information security programs, and states executive branch agencies, especially DHS, need to enhance their cyber analytical and technical capabilities.
Further, GAO charges individual agencies to develop and implement their own remedial action plans to resolve known deficiencies.
None of this will be easy, Wilshusen said.
"Even though progress has been made, this particular area is very dynamic," he said. "New threats emerge, and the landscape constantly changes, IT changes, and agencies are consistently adding new technologies and increasing the interconnectivity of their networks."



