Improving IT security by implementing better governance

As agency executives look to implement and reinforce cybersecurity as part of their overall IT and programmatic priorities, an important OMB policy and industry implementation framework can provide context and support by enabling sound IT governance.

In the face of ever-increasing cybersecurity risks, significant attention is being paid to improving agencies' preparedness and response to vulnerabilities and threats throughout the public sector. Two ways to go about supporting those activities involve addressing cybersecurity from a risk-based framework and engaging top-level leadership in addressing security as a strategic priority. A third complementary imperative involves establishing an overall IT governance structure that includes cybersecurity as a key enabler to achieving programmatic outcomes.
Fortunately, agencies have a number of tools at their disposal to enhance their governance framework.
1. OMB policy drivers for IT governance
At the end of 2008, the Office of Management and Budget reaffirmed and clarified the organizational, functional and operational governance framework required within the executive branch for managing and optimizing the effective use of IT. OMB Memorandum 09-02 established an IT governance framework that addresses the management structure, responsibilities and authorities of heads of departments and agencies and their CIOs in planning, acquiring, securing, operating and managing IT systems and assets within the department or agency.
The memo requires that agencies designate an executive-level CIO who reports to the head of the organization and has formal and full responsibility for all requirements set forth in statutes, regulations and public laws. That CIO also has ultimate responsibility for the governance, management and delivery of IT mission and business programs at the agency and must have an effective operative means of meeting that responsibility.
Furthermore, the CIO has the authority to set agencywide IT policy, including all areas of IT governance such as enterprise architecture and standards, IT capital planning and investment management, IT asset management, IT budgeting and acquisition, IT performance management, IT risk management and IT workforce management. The authority also extends to IT security and operations and IT information security, working with the agency chief information security officer and other security officials.
In August 2011, OMB issued related guidance in memo 11-29, which updated policy regarding the CIO's role in IT governance and explicitly discussed information security as part of the CIO's responsibilities. Taken together, those two OMB memos provide a strong framework for incorporating security considerations into overarching IT governance and strategy. That approach allows agency leaders to properly assess security risks in the context of risks and benefits from IT initiatives more broadly and from the programs that leverage IT and require good security to be successful.
2. An industry framework for implementation
One way to achieve the objectives of strong IT governance is to incorporate the COBIT 5 framework as a guide to implementing sound IT governance at the enterprise level. COBIT, which stands for Control Objectives for Information and Related Technology, serves as a business framework for the governance and management of enterprise IT and clearly defines IT governance as distinct from IT management. According to the COBIT 5 framework: "Governance ensures that stakeholder needs, conditions and options are evaluated to determine balanced, agreed-on enterprise objectives to be achieved; setting direction through prioritization and decision-making; and monitoring performance and compliance against agreed-on direction and objectives."
Furthermore, "management plans, builds, runs and monitors activities in alignment with the direction set by the governance body to achieve the enterprise objectives."
As technology use continues to increase the spread and impact of IT and cyber vulnerabilities and incidents, so do the tools and techniques to improve controls to protect key enterprise resources. The COBIT 5 framework is one of those tools. (COBIT 5 currently consists of the framework, two enabler guides, four professional guides, and COBIT 5 Online Collaborative Environment.) Moreover, COBIT 5 is one of the informative references contained in the National Institute of Standards and Technology's Cybersecurity Framework.
COBIT 5 is built on five basic principles and includes extensive guidance on enablers for governance and management of enterprise IT. Enterprises can use COBIT 5 framework principles to create optimal value by governing IT in a holistic manner, implementing comprehensive risk management and security controls, and ensuring that those controls are defined and implemented at a level appropriate to the increasing complexity of the enterprise.
The COBIT 5 framework delivers to its stakeholders the most complete and up-to-date guidance on governance and management of enterprise IT, as depicted in the graphic below.
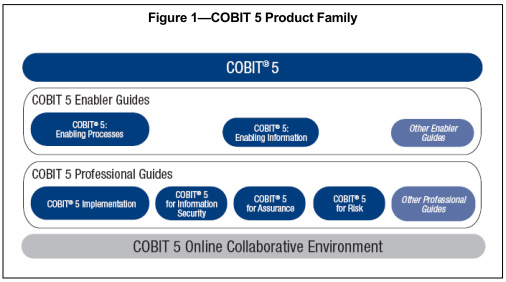
Image: ISACA
COBIT has proved to be very effective for implementing IT governance and detailed security controls globally at all sorts of institutions and a number of federal and state government agencies, including the Department of Veterans Affairs.
3. Sound IT governance can make a significant difference
In light of the constant changes in the IT environment, all enterprises should look to IT governance to secure information from the moment it is created to the time it is destroyed. That is why, in the past decade, IT governance has moved to the forefront of enterprise efforts to effectively manage and appropriately protect IT systems and assets, contributing to the success of risk-based security and supporting strategic decisions made by C-level executives across the public and private sectors.
Note: A version of this article also appears on the IBM Center for the Business of Government website.
NEXT STORY: GAO: TSA not making most of imaging tech


