NIH's big IT contract, FEMA's weather alert app, hacker-on-hacker attacks and more
News and notes from around the federal IT community.
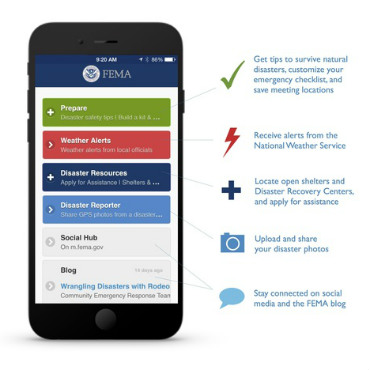
FEMA has unveiled new features for its popular weather app.
NIH awards $20 billion GWAC to 65 firms
The National Institutes of Health on April 14 announced the 65 vendors that will be on its $20 billion Chief Information Officer - Commodities and Solutions contract.
CIO-CS is a governmentwide acquisition contract run by NIH. Originally solicited in May 2014, it is the successor to NIH's Electronic Commodities Store III. It is intended to "support the full range of IT needs across the federal government with a particular emphasis on agencies involved in health care and clinical and biological research," according to NIH.
There are 58 value-added resellers on the contract, along with the following original equipment manufacturers: AT&T, Computer Sciences Corporation, Dell Federal Systems, HP, IBM, IMS Government Solutions and Vion Corp.
FEMA adds weather alerts to app
The Federal Emergency Management Agency unwrapped a new feature on its free weather app that allows users to get National Weather Service alerts for up to five locations across the country.
The latest version of the FEMA app is available for free in the App Store for Apple devices and Google Play for Android devices. Users who already have the app can download the latest update to add the weather alerts feature.
The new feature does not replace the Wireless Emergency Alerts function available on many new smartphones. WEAs, which have a special tone and vibration, are sent for emergencies such as extreme weather or AMBER alerts about missing children.
Report cites hacker-on-hacker cyber violence
A few months ago, a cyber-espionage hacker group in Southeast Asia that was probing governments and other organizations in the region wound up being targeted by another cyber-espionage group in what experts say is the first internecine battle among advanced persistent threat organizations.
A Kaspersky Lab post on April 15 said Hellsing, a small and technically unremarkable group that targets government and diplomatic organizations in Asia and the U.S., was subjected to a spear-phishing attack in 2014 by another threat actor called Naikon. Hellsing struck back with its own malware package.
Kaspersky said its experts noticed one of Naikon's targets, which turned out to be Hellsing, had spotted the attempt to infect its systems with a spear-phishing email message carrying a malicious attachment. Hellsing questioned the authenticity of the email with the sender and, apparently dissatisfied with the reply, did not open the attachment, according to Kaspersky. Shortly after that, Hellsing forwarded an email to Naikon containing its own malware aimed at identifying Naikon and gather intelligence on it.
Subsequent investigations by Kaspersky found that the recently discovered Hellsing has hit diplomatic and other government targets looking for intelligence in Malaysia, India, the Philippines and the U.S.
Information-sharing bill wins panel approval
The House Homeland Security Committee approved legislation April 14 that would encourage the voluntary sharing of cyberthreat information between the private sector and the government.
The bill, sponsored by Chairman Michael McCaul (R-Texas), was approved by voice vote.
The measure would provide liability protection to firms that share information on cyberthreats and their responses. The bill also would allow firms to conduct "network awareness" -- or the scanning or monitoring of information systems.


