GAO report highlights Einstein shortcomings
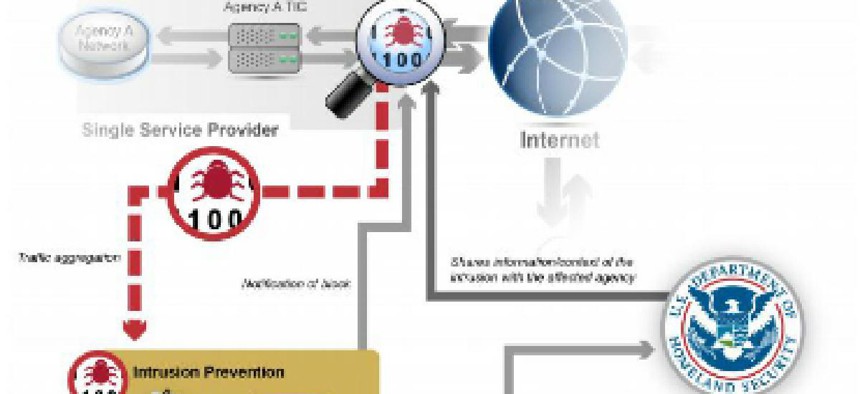
The Department of Homeland Security's Einstein program has built in limitations that prevent it from detecting previously unknown attack vectors, according to a watchdog report.

The Department of Homeland Security created the network protection program Einstein to combat threats to federal network. The program has cost $1.2 billion through fiscal year 2014, and is projected to cost $5.7 billion by the end of its lifecycle in 2018.
So what are agencies protected by the Einstein screen getting for all this money?
According to a new report from the Government Accountability Office, Einstein (the common name for what is officially known as the National Cybersecurity Protection System) only offers limited protection from cyber threats. The system can scan and intercept known threats, but it does not have the capacity to "employ other, more complex methodologies" to deal with unknown threats including zero-day exploits and to identify anomalous traffic that could indicate new, innovative attack vectors.
"By employing only signature-based intrusion detection, [Einstein] is unable to detect intrusions for which it does not have a valid or active signature deployed," the report stated.
In the wake of the devastating Office of Personnel Management hack, the White House ordered the acceleration of the deployment of Einstein 2 intrusion prevention services across agencies. But so far, those services – which entail the use of sensors to examine traffic – have been implemented at only five of 23 agencies, and implementation has been spotty even at participating entities.
Some problems include adapting Einstein to work with cloud email providers; challenges working with Internet service providers in the handling of classified threat indicators; and making sure there is adequate communication between CIO shops and network managers about Einstein on the agency side.
DHS Secretary Jeh Johnson stressed recent improvements to the Einstein program in a Jan. 30 statement in response to the public release of the report.
"The new and third phase of EINSTEIN, known as EINSTEIN 3A, has the ability to actively block -- not just detect -- potential cyber attacks. Unlike commercial products, EINSTEIN 3A can rely upon classified information, so the government is protected against our most sophisticated adversaries," Johnson said.
The DHS chief noted that in the wake of the hack of the Office of Personnel Management databases, Einstein 3A protection had been extended to 50 percent of the U.S. government, and is available to 100 percent. Prior to the breach, Einstein 3A was available only to 20 percent of the government.
In reply comments included in an appendix in the GAO report, DHS' Jim Crumpacker said that "no single system provides a cybersecurity 'silver bullet,' and noted that "it is essential for agencies to implement defense-in-depth," to defend agency systems at multiple spots. Einstein, Crumpacker said, "is one of several tools that can enhance the management of cyber risks," but "it needs to be a joint effort between DHS and the departments and agencies deploying the [Einstein] capability to be fully successful."
GAO offered nine recommendations, including upgrading the system to target unknown threats, and improving its ability to scan encrypted traffic, IPv6 traffic and traffic across industrial control systems. GAO also wants updates to Einstein's signature management system, better metrics for Einstein to measure intrusion detection and interception, and better tools do pick up on threats inside an agency's network.
DHS concurred with all the recommendations. In addition, agency officials noted DHS was working to make sure security requirements that spell out agency and vendor obligations for protecting networks are included in the Network Solutions 2020, the next-generation contract vehicle for ISP services that is being developed to succeed Networx.
This article was updated Jan. 31 to include comments from DHS Secretary Jeh Johnson.


