DHS: WannaCry could linger
The virulent ransomware could worm its way into day-to-day business operations of critical infrastructure providers, DHS warned.
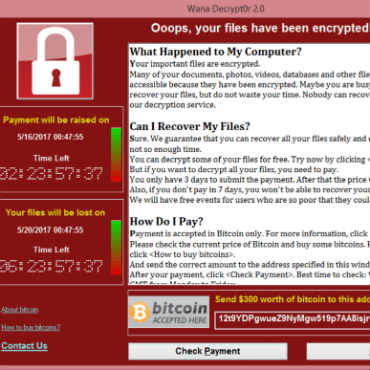
In the days following the massive WannaCry ransomware attack that infected hundreds of thousands of computers worldwide, the Department of Homeland Security told critical infrastructure providers they would be less affected by the malware than consumers -- but that they should continue to be on guard.
The unclassified memo, sent out on May 14 and posted on the Public Intelligence open-source website on May 28, told critical infrastructure providers that WannaCry was aimed at day-to-day business systems, not their critical operational IT. The exploits that formed the basis of the malware were allegedly obtained by the hacker group Shadow Brokers from the National Security Agency.
The WannaCry attack that began on May 12 infected almost 300,000 computers in 50 countries, largely by leveraging a gap in aging Windows software that had been left unpatched. It hit the U.K.'s National Health Service, Spain's Telefónica, as well as international operations of corporations such as FedEx.
The impact in the U.S. was relatively minimal. Even so, DHS warned critical infrastructure providers such as electric companies and financial service providers that the malware might show up in their business systems. Catastrophic failure of operational systems, however, was unlikely, DHS said.
"Impacts will be largely financial from business interruption" to critical infrastructure owners and operators' business control systems, said the memo, and not to process control systems.
The memo, prepared by DHS' Office of Cyber and Infrastructure Analysis said the biggest impact for critical infrastructure providers "will be short-term financial losses from business interruption, some of which could be covered by cyber insurance, based on a review of previous ransomware attacks."
The OCIA warned, however, that if some critical infrastructure providers' industrial control systems used similar IT components as their business control systems, those systems could be theoretically affected.
One critical infrastructure area, in particular, could face significant impact from a WannaCry "variant," it said, given its impact on the United Kingdom's National Health Service. The "kill switch" variant could deny healthcare providers access to health systems and Internet-connected devices.
OCIA said although the impact of the attack on the National Health Service hadn't been fully reported, although "they illustrate that larger-scale attacks can affect patient care on a regional or national level."
Even with the relative reassurance that a "catastrophic impact" to infrastructure operational IT is unlikely, OCIA said compromises of infrastructure providers' business system could cause the same damage that data breaches have had on big corporations, including stolen data, personally identifiable information, intellectual property and financial information.


