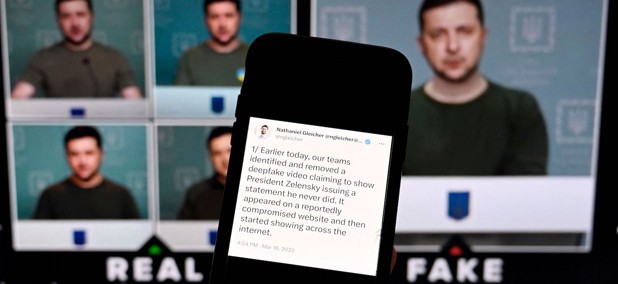
Cybersecurity
The imitation game
The emergence of low-cost deepfakes has led to a high-stakes race to develop technologies that can detect and label synthetic media.
Acquisition
Lawsuit upends $4B DHS software buy
A push to buy a modernized DHS financial management system is being held up by another court battle, one that threatens to again upend a project that already suffers from a long history of failure.
Modernization
Cyber, but in space
A White House memo proposes that space-based technology must have cybersecurity built in at the design stage while also allowing flexibility for operators to adapt on the fly.
Modernization
FCC estimates $1.8 billion to replace Huawei, ZTE telecom parts
The agency also released a list of 51 firms that would qualify for reimbursement, spanning from smaller telecoms to large vendors like Verizon and CenturyLink.
Cybersecurity
CISA, White House release vulnerability disclosure policies
The Office of Management and Budget and the Cybersecurity and Infrastructure Security Agency have released a memorandum and Binding Operational Directive guiding federal agencies on how to set up their vulnerability research and disclosure programs.
Cybersecurity
OMB tees up supply chain regs
The interim regulation sets down rules for excluding vendors from federal procurement if an interagency panel deems them untrustworthy.
Cybersecurity
CISA bug bounty directive awaits White House blessing
A draft policy from the Cybersecurity and Information Security Agency instructing agencies to create vulnerability disclosure programs to allow third-party bug hunters to flag security vulnerabilities in federal systems is all-but-completed, sources say.
Digital Government
Experts tout election security gains since 2016
While threats to election infrastructure endure, experts are telling the public not to lose sight of the many security gains that have been put in place over the last four years.
Cybersecurity
The risks of supply chain threat sharing
Some of the most valuable data around supply chain threats – identifying suspicious or untrustworthy actors -- can often be legally perilous to share.
Digital Government
Disinformation on the cheap
Online influence operations are often easy and cheap to set up with open source tooling, according to new research from Cisco Talos.
Cybersecurity
Trump nominates Chad Wolf as permanent DHS chief
Wolf has served as acting secretary since November 2019 but is currently embroiled in a controversy over the legitimacy of his appointment.
Modernization
IRS legacy system problems could be worse than advertised
A new watchdog report finds additional systems and applications that would be considered legacy under the IT organization's own definition, and hundreds more that might or might not.
Cybersecurity
Voice phishing attacks on the rise, CISA, FBI warn
An industry alert warns of an increasingly sophisticated social engineering campaign since July that is targeting VPNs and teleworkers.
Cybersecurity
CISA infrastructure chief Brian Harrell resigns
The assistant director, charged with helping to protect critical infrastructure from physical and cyber threats, will be returning to the private sector, the agency confirmed.
Cybersecurity
With the clock ticking, a House committee looks to election security
Election readiness, the cybersecurity fallout from COVID-induced telework and network monitoring and will be key areas of focus for House Homeland Security Democrats this year.
Cybersecurity
CISO Schneider exits OMB for Venable post
Federal Chief Information Security Officer Grant Schneider is leaving the federal government to take a job at Venable.
Modernization
U.S. imposes new restrictions on Huawei, semiconductor industry
The Department of Commerce is tightening rules targeting the Chinese telecom's supply chain around computer processing chips and restricting sales of chips made with U.S. technology.
Cybersecurity
GAO: DHS acting secretary, top deputy were appointed illegally
Top acting officials at DHS were appointed without regard for laws in place governing agency succession, according to a Government Accountability Office legal opinion.
Cybersecurity
FBI, NSA reveal undisclosed Russian hacking tool
The GRU malware targets Linux operating systems and is used to conduct cyber espionage on behalf.
Digital Government
Lag continues for federal voting system standards
The election community wants the EAC to speed up its process for approving new voting system standards. Public comments on draft requirements show there are still numerous unresolved conflicts to hash out.
Almost There!
Help us tailor content specifically for you: