People
Avocent to buy LANDesk for up to $476M
The purchase will allow federal IT managers to streamline the tools and processes they use to manage IT in large, distributed environments, a company official said.
Cybersecurity
Checklist outlines new cyberthreats
The Cybersecurity Checklist looks at potential vectors for real-world cyberattacks and recommends ways to thwart them.
People
DHS ramps up TWIC program
By the end of summer, DHS will check the backgrounds of 400,000 port workers, Chertoff said.
People
UPDATED: Beaming across the border
DHS and State disagree on which security technology to use for border protection
Modernization
In-Q-Tel head resigns
Just months after taking the position to lead CIA ventures, Yoran unexpectedly steps down, citing a desire to be home more.
People
Feds look to ants, wikis and blogs
The CIA already has more than 1,000 internal blogs and an internal wiki with about 10,000 pages.
People
Lee: FEMA working on biz relationships
She said the agency is emulating DOD's practices before the 2006 hurricane season starts.
People
InfoZen wins $148M TSA contract
Company will be responsible for overseeing systems in the Office of Transportation Threat Assessment and Credentialing.
People
DHS: E-passport live test a success
The agency is on track to meet its Oct. 26 deadline for use of the passports.
People
US-VISIT chief wants tougher border security
As the PASS card program is in development, Jim Williams wishes for more ways to spot criminal suspects and possible terrorists.
People
UPDATED: GAO: Feds must standardize info-sharing policies
The 26 agencies it reviewed have 56 different sensitive-but-classified designations.
Modernization
Military branches can now IM
The services are using Bantu's Inter-domain Messaging gateway to chat and conference.
Modernization
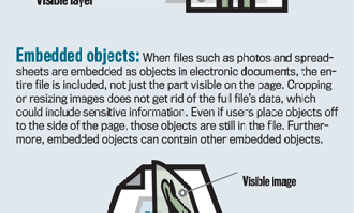
Accidental publicist
Agencies are risking the unwitting release of sensitive information using popular office software.
Modernization
Pentium computers vulnerable to cyberattack
Security experts warn of that and other risks at CanSecWest/core 06
Cybersecurity
Cyberattackers can exploit Pentium self-defense
The vulnerability affects every computer that runs on x86 architecture, an expert said at the CanSecWest/core06 conference.
Cybersecurity
Time for a new look at security
Intelligence community experts plan to streamline their security procedures.
Modernization
GAO: Common Criteria is not common enough
Auditors say the process takes too long and its effectiveness is not well-understood.
People
DOJ, DOD stress self-powered communications
The departments say Hurricane Katrina exposed the need for technology that can operate without a traditional infrastructure.
Cybersecurity
Security system checks take too long, experts say
Current certification and accreditation processes for federal information systems don’t reflect the modern network environment, a panel said today.
Cybersecurity
Video surveillance gets smart
Integrated systems are evolving from mere watchers to security enforcers.
Almost There!
Help us tailor content specifically for you: